| vuln.sg Vulnerability Research Advisory |
by Tan Chew Keong  Summary
Summary
A security issue and a vulnerability have been found in HP HPeDiag ActiveX Controls. When exploited, the security issue and vulnerability allow the disclosure of system information and execution of arbitrary code when the user views a malicious website. These ActiveX controls are installed as part of HP Software Update version 3.0.2.991 when the user installs the Windows software suite for HP color LaserJet 2820/2840.  Tested Versions
Tested Versions
Installing HP SoftPaq SP38202 does not resolve the issue since it disables only the HPRulesEngine.ContentCollection.1 control.  Details
Details
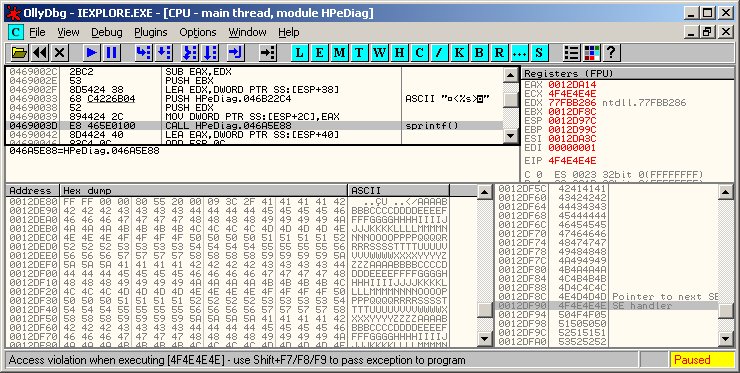
This advisory discloses a security issue and a vulnerability in HP HPeDiag ActiveX Controls. These ActiveX controls are installed as part of HP Software Update version 3.0.2.991 when the user installs the Windows software suite for HP color LaserJet 2820/2840. Successful exploit requires that the user is tricked into visiting a malicious website using IE6 or earlier. If the user uses IE7, he must first be convinced into allowing the ActiveX control to run. 1) Stack-based Buffer Overflow in HPeSupportDiags.HPIniFileUtil.1 (93441C07-E57E-4086-B912-F323D741A9D8) The buffer overflow occurs within the GetXmlFromIni method of the HPeSupportDiags.HPIniFileUtil.1 ActiveX control when creating XML output from an INI input file. This control is marked "safe-for-scripting" and hence, can be invoked from Internet Explorer. In this method, each Section name that is read from the INI input file is used in an unsafe sprintf() call to construct the XML output. This causes a stack-based buffer when the Section name is overly long. To exploit this vulnerability, the attacker must be able to create a webpage that uses the GetXmlFromIni method to process an INI file that is accessible by the victim. By placing the malicious INI on a publicly accessible Windows shared folder, it is possible for the attacker to trigger this buffer overflow without having to first place the INI file on the victim's system. The ActiveX control is compiled with VC++ stack-based buffer overflow protection. However, in this case, the vulnerability is still exploitable since it is possible to overwrite the saved SEH. When the buffer overflow happens, a write-access exception is triggered that passes control to the overwritten SEH before the function returns. By spraying the IE heap with shellcode and overwriting the SEH with an address that points into the IE heap, a reliable exploit can be achived. The vulnerable code exists in HPeDiag.dll version 1.0.11.0. The Ollydbg screen capture below shows that the vulnerability can be used to control EIP by overwriting the saved SEH.
2) System Information Disclosure in other ActiveX Controls. Several other ActiveX controls are marked "safe-for-scripting". This can be used by a malicious website to gather system information. Examples of these ActiveX controls include the following. NOTE: This is not an exhaustive list. Please set the kill-bit on all unnecessary controls.
 POC / Test Code
POC / Test Code
POC HTML files have been provided to the vendor to reproduce the issue. Instructions:
 Patch / Workaround
Patch / Workaround
Update to HP Software Update version 4.000.010.008 or later using HP Software Update. See release notes. Vendor advisory is here.  Disclosure Timeline
Disclosure Timeline
2008-03-15 - Vulnerability Discovered. |
| Contact |
| For further enquries, comments, suggestions or bug reports, simply email them to |