| vuln.sg Vulnerability Research Advisory |
by Tan Chew Keong  Summary
Summary
A vulnerability has been found in IBM Lotus Notes. When exploited, the vulnerability allows execution of arbitrary code when the user views a malicious WordPerfect file.  Tested Versions
Tested Versions
 Details
Details
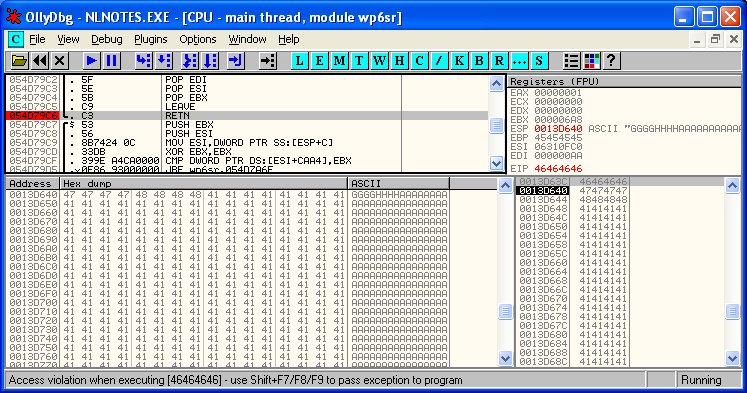
This advisory discloses a buffer overflow vulnerability in IBM Lotus Notes. The stack-based buffer overflow occurs when the user views a WordPerfect (.wpd) file (that was received as an email attachment) from within Lotus Notes. It is possible to exploit the buffer overflow to execute arbitrary code. In order to exploit this vulnerability successfully, the user must be convinced to view a malicious WordPerfect file attachment using the built-in viewer in Lotus Notes. The buffer overflow occurs within the wp6sr.dll DLL in the function that reads the document properties (e.g. Title, Subject, Author) from the WordPerfect file. The function uses a byte from the WordPerfect file as a counter to copy the contents of the WordPerfect file from a heap-buffer to a 2400-byte stack-buffer. This byte is multiplied by 256, before it is used as a counter. So the maximum value of the counter is 0xFF * 256 = 65280. By manipulating this byte in a specially-crafted WordPerfect file, it is possible to cause more than 2400 bytes to be copied from the WordPerfect file into the stack buffer. This overwrites the saved EIP and SEH, and can be exploited for arbitrary code execution. The Ollydbg screen capture below shows that the vulnerability can be used to overwrite the saved EIP.
 POC / Test Code
POC / Test Code
The following POC WordPerfect (WPD) file will exploit the vulnerability in IBM Lotus Notes to execute the harmless calculator (calc.exe). The POC has been successfully tested on English Windows XP SP2 with Lotus Notes version 7.0.2.
Instructions:
 Patch / Workaround
Patch / Workaround
Update to version 7.0.3. See vendor's technote for more information.  Disclosure Timeline
Disclosure Timeline
2007-01-01 - Vulnerability Discovered. |
| Contact |
| For further enquries, comments, suggestions or bug reports, simply email them to |