| vuln.sg Vulnerability Research Advisory |
by Tan Chew Keong
 Summary
Summary
A vulnerability has been found within the Web Server functionality of Ice Cold Apps Servers Ultimate and HTTPS / FTPS / SFTP Server. When exploited, this vulnerability allows an anonymous attacker to download files from arbitrary locations on a user's Android device.  Tested Versions
Tested Versions
 Details
Details
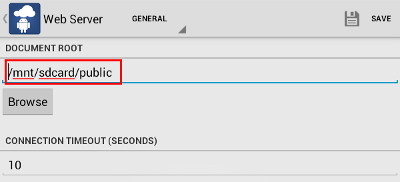
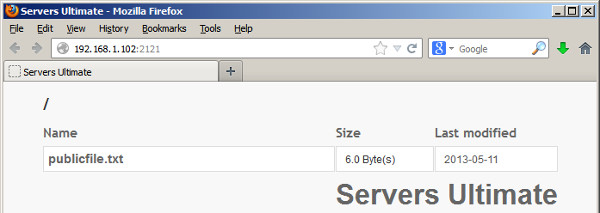
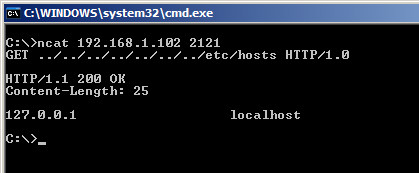
This advisory discloses a vulnerability within the Web Server functionality of Ice Cold Apps Servers Ultimate and HTTPS / FTPS / SFTP Server. When exploited, this vulnerability allows an anonymous attacker to download files from arbitrary locations on a user's Android device, including files in other subdirectories under /mnt/sdcard/ where the user may not have any intension to share. The Web Server functionality does not properly sanitise HTTP requests containing directory traversal sequences ../ that are received from a browser. This allows a malicious attacker to download files from arbitrary directories from the user's Android device.  POC / Test Code
POC / Test Code
The instructions below illustrates how this vulnerability can be reproduced using Servers Ultimate. The steps for reproducing the vulnerability on HTTPS / FTPS / SFTP Server are very similar, and hence, will not be repeated.
 Patch / Workaround
Patch / Workaround
Fixed in Servers Ultimate version 5.8.0 and HTTPS / FTPS / SFTP Server version 4.6.1 Vendor's advisory here.  Disclosure Timeline
Disclosure Timeline
2013-05-10 - Vulnerability Discovered. |
| Contact |
| For further enquries, comments, suggestions or bug reports, simply email them to |