| vuln.sg Vulnerability Research Advisory |
by Tan Chew Keong
 Summary
Summary
A directory traversal vulnerability has been found in PKWARE SecureZIP Reader for Android. When exploited, this vulnerability allows an anonymous attacker to write files to arbitrary locations within the SD card of the user's Android device.  Tested Versions
Tested Versions
 Details
Details
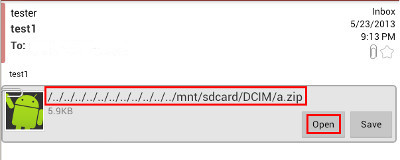
This advisory discloses a directory traversal vulnerability in PKWARE SecureZIP Reader for Android. When exploited, this vulnerability allow an anonymous attacker to write files to arbitrary locations within the SD card of the user's Android device. When SecureZIP is installed on an Android device, it is registered as the handler for the URI type content:// with mime-type application/x-zip-compressed. This allows it to be used by email clients to open ZIP file attachments in emails. When the user, clicks a ZIP file attachment in an email, he will be given a choice to choose from list of handlers that are able to open the ZIP attachment. When SecureZip is choosen, it will query the email client (content provider) for the display name and the content of the ZIP attachment. SecureZIP does not properly sanitize the value of the returned display name before using it create a temporary filename to store the ZIP attachment. If the display name contains directory traversal sequences, the resulting temporary file will be written by SecureZip outside of SecureZip's temp directory. This can potentially be exploited in conjunction with an email client to overwrite files in arbitrary locations within the SD card of the user's Android device. More specifically, an attacker can send a user an email containing a ZIP file attachment with directory traversal sequences in the attachment filename and tricking the user to open the attachment from the email client using SecureZIP. Without disclosing too much details, it has been confirmed that there are indeed email clients that allow this to be exploited. A screenshot from one such email client is shown below.
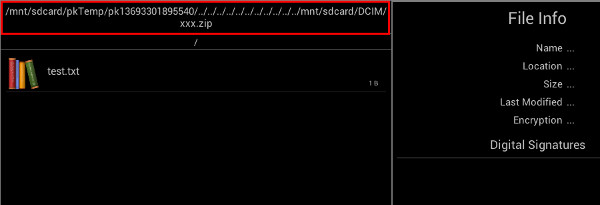
To make matter worse, SecureZIP will recursively delete the entire temp directory when it exits. This potentially allows an attacker to exploit this vulnerability to delete entire directories from the user's SD card. An example of a display name with directory traversal sequences returned by an email client is shown below. /../../../../../../../../../../../mnt/sdcard/DCIM/xxx.zip As can seen in the log trace from SecureZip below, it is clear that directory traversal exists, the entire "temp" directory will be recursively deleted after use: 05-24 01:29:49.550: I/ArchiveExplorerActivity(2556): Saving a copy of mail attachment to: /mnt/sdcard/pkTemp/pk13693301895540/../../../../../../../../../../../mnt/sdcard/DCIM/xxx.zip 05-24 01:29:49.550: I/ArchiveExplorerActivity(2556): (DELETEME) Archive Path: /mnt/sdcard/pkTemp/pk13693301895540/../../../../../../../../../../../mnt/sdcard/DCIM/xxx.zip 05-24 01:29:49.550: D/ArchiveUtils(2556): Opening zip archive /mnt/sdcard/pkTemp/pk13693301895540/../../../../../../../../../../../mnt/sdcard/DCIM/xxx.zip 05-24 01:29:49.560: I/ArchiveUtils(2556): No cached ZipFile instance found for: /mnt/sdcard/pkTemp/pk13693301895540/../../../../../../../../../../../mnt/sdcard/DCIM/xxx.zip 05-24 01:29:50.560: I/CleanupService(2556): Deleted /mnt/sdcard/pkTemp/pk13693301895540/../../../../../../../../../../../mnt/sdcard/DCIM/xxx.zip 05-24 01:29:50.570: I/CleanupService(2556): Deleted /mnt/sdcard/pkTemp/pk13693301895540/../../../../../../../../../../../mnt/sdcard/DCIM/xxx/test.txt 05-24 01:29:50.580: I/CleanupService(2556): Deleted /mnt/sdcard/pkTemp/pk13693301895540/../../../../../../../../../../../mnt/sdcard/DCIM/xxx 05-24 01:29:50.580: I/CleanupService(2556): Deleted /mnt/sdcard/pkTemp/pk13693301895540/../../../../../../../../../../../mnt/sdcard/DCIM  POC / Test Code
POC / Test Code
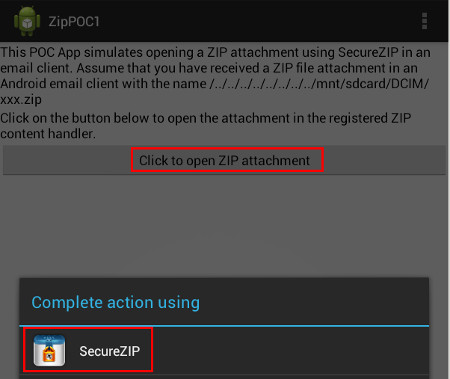
Please download the POC here and follow the instructions below. The POC runs on Android device and simulates an email client that delivers a Zip attachment to SecureZip with directory traversal sequences in its display name. Instructions for Testing the Vulnerability:
 Patch / Workaround
Patch / Workaround
Update to version 1.00.0021 via the Play Store.  Disclosure Timeline
Disclosure Timeline
2013-05-24 - Vulnerability Discovered. |
| Contact |
| For further enquries, comments, suggestions or bug reports, simply email them to |